Streaming GitHub audit log to S3 with OpenID Connect - Troubleshooting
Table of Contents
Streaming GitHub audit log to one centralized place is quite often used to maintain compliance or improve security within the organization, or both.
If you are reading this post, you are having trouble setting up this stream to your AWS S3. I will show you two common mistakes that I experienced and solved.
First steps #
GitHub has good documentation on how to configure communication between GitHub and AWS.
You can find it in Streaming the audit log for your enterprise. The first step I would recommend is to go through the steps again and check if you did everything listed there. If you did and still have a problem, carry on reading.
What does the successful setup look like? #
Before you will be able to save streaming, you need to go through the “Check endpoint” process. Successful communication will be shown as:
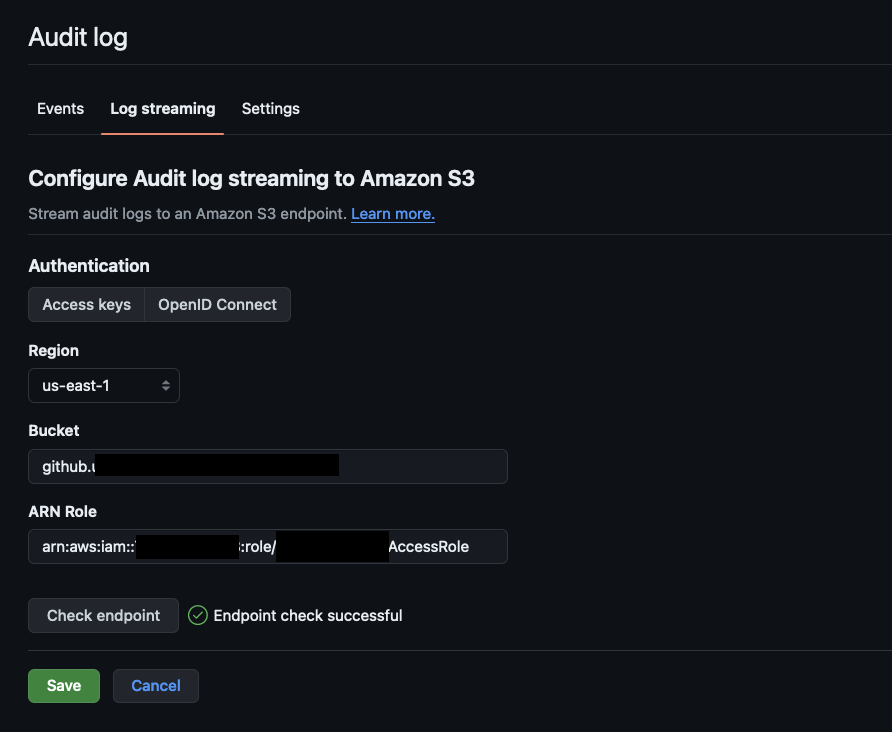
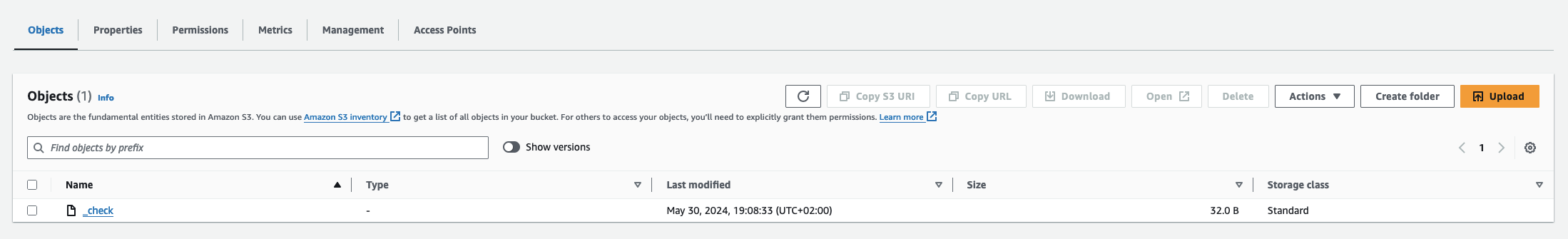
Also, in your bucket, you should have a _check object:
Errors #
So as we know what a successful setup looks like, let us check what potential issues we can face.
There was an error trying to connect to XYZXYZXYZ #
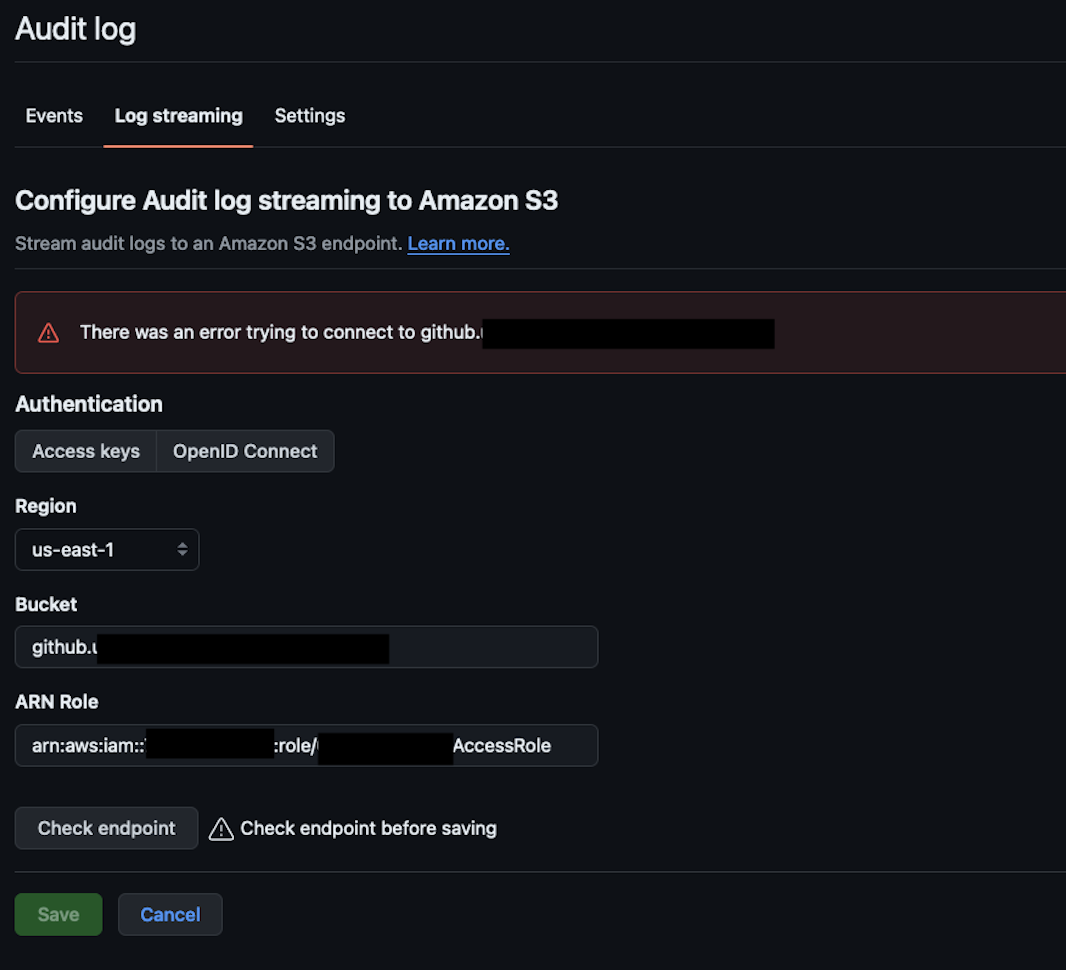
This error can indicate that there is something wrong with your OpenID configuration or IAM role configuration.
To confirm that, just go to the IAM role that you’ve used and check its “Last activity.” If its value is set to -, it means it was never assumed by a third party (in this case GitHub).
So double-check that:
- trusted entities are set correctly
- your thumbprints in the Identity provider are correct. How to get one you can read in Obtain the thumbprint for an OpenID Connect identity provider
Authorization error accessing “XYZXYZXYZ” bucket. #
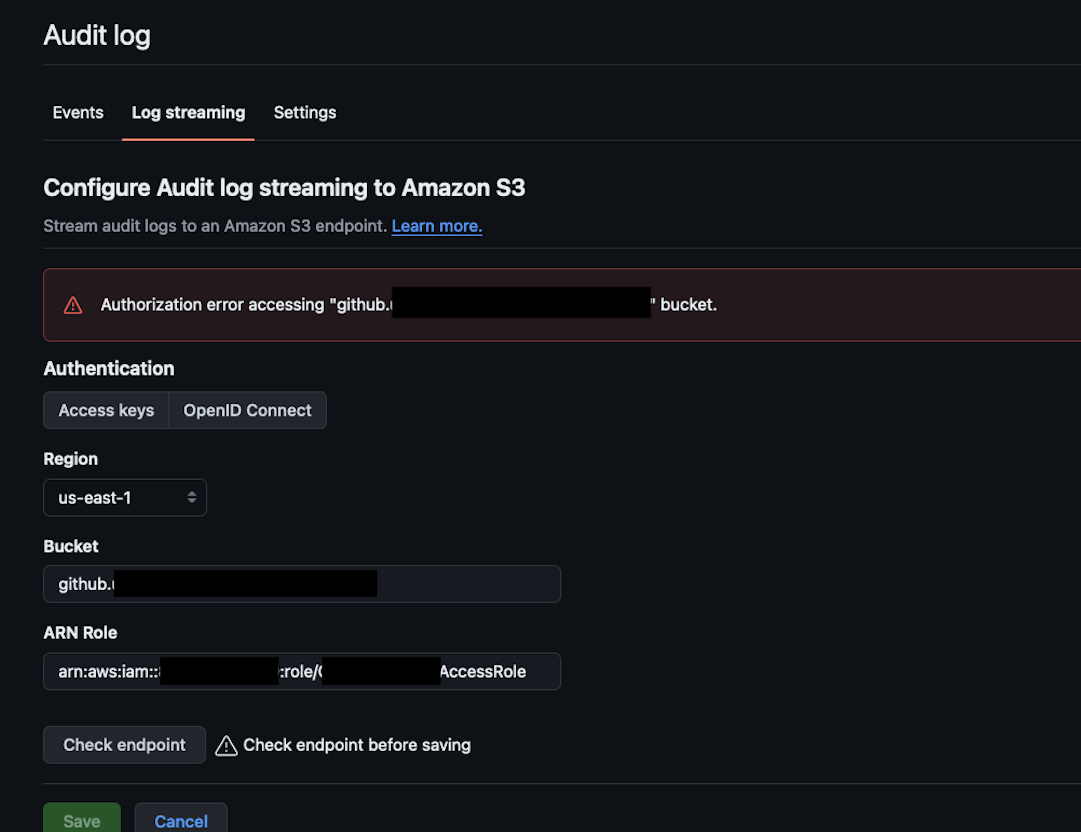
So you definitely confirmed that your OpenID connection is working correctly? Make sure that the role you want to use has “Last activity” set to some real date.
If you did that, and you see this “Authorization error accessing “XYZXYZXYZ” bucket.” it might indicate at least these two things:
Your role does not have access to S3 bucket #
Make sure that your role has the permission set:
{
"Effect": "Allow",
"Action": [
"s3:PutObject"
],
"Resource": "arn:aws:s3:::{your-bucket-name}/*"
}
You use custom KMS as default encryption #
If you use “Server-side encryption with AWS Key Management Service keys (SSE-KMS)” for your S3 bucket, the role that will be assumed by GitHub needs to have access to it as well.
Make sure that your role has:
{
"Effect": "Allow",
"Action": [
"kms:Encrypt",
"kms:ReEncrypt",
"kms:GenerateDataKey"
],
"Resource": "arn:aws:kms:{aws-region}:{aws-account-id}:key/{kms-key-id}"
}
The End #
That’s it! I hope you found something useful in this post! If your company needs some help with AWS, get in touch.
